Bypass keying, a masterkeying specialty, is a form of controlled cross keying, primarily used where there is an office suite with an external door and a number of offices within that suite. The front exterior door is operated by any of the interior door keys. This allows users to carry a minimum amount of keys to get into their space and may avoid confusion as to which key to use.
The basic principal works at the key bitting array stage of masterkeying. I will work one example to show how it operates.
Our example suite is a submaster of the overall building key system. If it is the latter, then you need to break it down to the submaster level and isolate the bittings that you will be using for this submaster and work with that block only.
As an example, the key bitting array is:
Top master: 105494
Submaster (usually the page master): 321494
Or block master if a smaller system: 321490
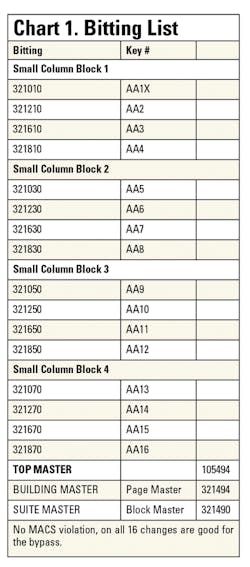
I will work with the block master for simplicity in explanation. See Chart 1 for a page of a progression array.
Start at the vary chamber (fourth chamber). The progression 0-2-6-8 for each small column-block determines the bitting that will work this particular bypass cylinder. How large a bypass will you need? One will need to size the overall number of keys meant to work this bypass, taking into account the number of rooms that are necessary for a rekeying. In my example there are 7 spaces in the suite, and some future capacity needs to be built in for future rekeying. The actual number of bittings used is determined by the keying that is used here, determined in advance by the keying meeting with the customer.
Normally, the most varied chamber is what is called the "stack." In this case, it is the fourth chamber in the progresssion array that changes with every bitting. So in this example the stack is 0-2-4-6-8, and when mastered or "stacked" with the 0 bottom pin, and four two-step master pins, topped off with a top pin and spring, this chamber will work with keys cut to 0, 2, 4, 6, orn 8. Even if all the rest of the cuts on the key remain constant, you will still have five possible keys operating this chamber, one master key and four change keys.
To increase the number of changes that can be applied to the bypass, move to the next most varied chamber in the progression. In this case the next small column block in cue, which is the fifth chamber. The fifth chamber changes with every four-bitting block. This could be mastered for another four changes. This will then result in a total of 8 changes. As this continues, adding another master pin on top of the last, will add four changes each time it is mastered, until it reaches a natural break point.
One break point where the limit cold be hit is when the block master is exhausted. This will produce two fully stacked chambers. So using progression and probability math, this would b 4 times 4 = 16 changes that could be applied to the bypass. It is usually a good idea to set the bypass at the block master limit so that there is available capacity. But it could be set to be more selective too, that is to set the bittings in one small column block to be bypassed (a full stack and one master pin; four usable bittings), or two small column blocks (a full stack and two master pins stacked on each other; for 8 usable bittings), or even three small column blocks (a full stack and 3 master pins stacked on each other; for 12 usable bittingss), leaving the rest in reserve, so long as those bittings are held in reserve too. This way one will selectively choose which bittings will operate a particular bypass.
Lastly as the most used option, we can supply all four small column blocks (a full stack in the 4th chamber and a second full stack in the 5th chamber). Thus we have isolated an entire block of this page master for this bypass to the intended suite. This should be an appropriate size submaster key system for this size suite, with spares for rekeying and a suite master. Although I have set aside the entire block for bypass use, I did not lose any bittings for use in this submaster system. The bittings themselves can still be used for their intended rooms, however I did enable that bittings's bypass capability, and if I so choose to pin it into the suite door, to activate that bitting's bypass function for use, I can do so without impact upon the office doors.
See Chart 2 for a representation of the bitting list developed. Take a close look at the block and we will now start assigning the key codes to thse bittings. I will always assign the first change as the individual code and bitting for the bypass cylinder itself, and only the bypass cylinder. This bitting is not to be applied to any other office or application other than the bypass cylinder. It is from my experience that it is always good to have a key only for bypasses, and not anything else. In some cases an employee may only need access to the suite and copy room and not to any offices. The key code assigned to this bypass can also become an identifier with an X behind it denoting a bypass cylinder.
So to create the bitting list, I develop it from this block of the master key page. With all the bittings listed fully, I can get an overview and also account for maximum adjacent cut problems (MAC). MAC may eliminate some of the bitting off the list. In this case all 16 changes can be used.
Once all the bittings are listed, and they are usable, I start assigning the key codes to these bittings. In other words, cylinder AA1X will be operated by keys AA1 to AA16 and also by the suite (block) master, building or floor master (page master) and the top master (building or grandmaster).
On the bitting list a note is made - op. by AA1-AA16. The X applies to the cylinder usually to identify it as a bypass. An "X" may or may not be applied to the key itself. Now with the bitting list fully developed, I can apply these key codes to the appropriate door. Of course the whole reason for this exercise was to create a bypass cylinder. So now is the time to apply these codes. Let me start with the bypass first.
Let me backtrack a little here. The first thing that should have been done in creating the masterkey system of this facility was to sit down in a keying meeting with the owner or representative of either the facility or the end-user. Everything from sizing the masterkey system, type of system (grandmaster or not; existing system add-on or not), submasters, and of course the bypass, and where all these are to be applied, flows from this keying meeting. One should have a very clear idea of where the bypasses should be applied. So at this stage once the bypass is assigned its number and the X suffix, it gets assigned onto the floor plan, for the bypasses. Then depending on key alike groups or key different masterkeying, apply as appropriate using the codes according to the key plan. If building from scratch, it would be a good idea to assign the actual code to be used. That is why I am consistent with using the first code detailed as **1X as the bypass. Now it's a matter of having a bitting to go with it. As stated before, this meeting will determine how many bittings to setup the bypass with and the overall size of this masterkey system.
If the first block that was chosen becomes the first bypass for the first suite, then a second block can be picked out of that page of the progression array and the same done; that could be the bypass for the second suite. It is from my experience that if an office suite exists, there usually is one across the hall too. So when keying an entire building, the second bypass will be important. Because it is from a different block, and that block master is the suite master, there is no possibility of one set of keys in suite A to operate suite B across the hall. Even though 99 percent of the keying is identical to each other, that 1 percent will keep suite A keys from operating suite B and vise versa.
A shortcut is to leave a stack chamber empty. This has its advantages and disadvantages to be determined by the application of the bypass. Of course having all the pin tumblers in the stack chamber provides more security than an empty one, but if there are issues of the stack jamming due to worn keys or worn cylinders, and no one seems to want to replace their worn keys, it may be better to leave the chamber empty, especially if you determine that what the bypass cylinder is protecting is low security. As example: going into an empty main suite or conference room with only tables and chairs. If there is valuable equipment in either space, then that affects the decision to leave a chamber empty or not.
When customers are given bypass keying as an option, they are usually quite impressed. From my experience, I can tell you that the bypass keying option is rather popular. It cuts down on the number of keys carried, makes it simpler for the end user, and in some cases encourages the locking of certain doors that may otherwise be left unlocked.
But a caveat is to be forewarned. If the bypass itself needs to be rekeyed, selectively deactivating a key out of the bypass may be either difficult or impossible and involves a time-consuming calculation. Other options to mitigate this caveat are to:
- Set only half the bittings on the bypass if size is allowable. The first two small column-blocks for bypass 1, the last two column-blocks held in reserve for rekeying bypass 2. The only advantage to this is in keeping the existing sub-master key. All the other rooms still need to be rekeyed to bittings on bypass 2.
- The only other viable option is to rekey the exterior door onto one of the available bittings meant for an office do0or. The remove the bypass system and give everybody another key to carry.
- If that is not a good option, then redo the entire bypass system using a new sub-master key.
Despite these caveats, bypass keying is more controlled than other forms of cross keying. For one, you will know it works only under a specific submaster system, and will not interchange with other sub-masters. You can set the limits as required. Although using just a single block master here was used as an example, this method can be expanded to larger sub-masters if necessary. It can even be a sort of masterkeying for a common area in the building rather than just for a suite of offices. Perhaps everyone should have access to a pantry or kitchen area, but the kitchen or pantry may need to be locked to keep unwanted guests out of the food. This application would be ideal for bypass keying, as everybody needs to get in, but it also must stay locked.
David T. Lee is key control specialist for George Mason University.