Kaba AD102 Kit Opens The Door To Biometrics
In electronic access control vernacular, authentication is how a system determines if the individual requesting permission to enter is allowed (authorized).
Authentication is achieved several different ways:
- What a person has: such as a credential or a key
- What a person knows: such as a code, often referred to a P.I.N. (personal identification number)
- Who a person is: a physiological feature of the individual, such as a fingerprint, hand geometry, retinal pattern, or facial features.
The more authentication factors used to qualify the individual the better the security. For example, a single numeric entry code for all users is considered the weakest authentication. A memorized code can be easily shared or even guessed so security cannot be assured.
Using a key or credential is generally better authentication. However, how well the keys or credentials are managed and the type of key or credential used will affect security. For example, a non-patented key can be readily duplicated just about anywhere. Additionally if a credential is lost or stolen but remains in the system, or if a key - even a high security key - is lost or stolen and the locks are not rekeyed, security of the opening is compromised.
If a credential or key is used in conjunction with a memorized code, this is referred to as dual or multiple authentication, and this greatly enhances security.
In electronic access control, biometrics is considered the highest level of authentication, and biometrics can be used in single factor or multiple factor security management.
Variables such as the reliability of the biometrics and other elements of the premises security management system affect the system’s efficacy.
A fingerprint or other biometric factor is stored electronically and referred to as a template. Depending on the particular application, the template is used in different ways. In some applications, the template is embedded onto a credential, and the person requesting access presents the credential at the access control point, at which time their system compares the template on the credential with the physical characteristic of the individual requesting access. The biometric reader compares the person’s biometric characteristic with the single template stored on the credential, performing a 1 to 1 comparison.
The credential itself is usually proximity encoded and is also enrolled into the system so that the template may be paired with the person’s identity and data, and access privileges can be managed using the credential within the access control database. Often, different levels of authentication are required at different locations within the premises, card only at some openings, and biometric and credential at others.
Some biometric systems such as the KABA AD102KIT are standalone and use a keypad rather than a card reader. The person presents his finger and the system tests the biometric characteristic against the templates stored in the standalone system’s database. This is called a one to many comparison.
The AD102KIT, like other biometric units in this class, allows each user to enroll more than one finger, and will also allow a P.I.N. to be associated with each user. When using this method, having a dirty or damaged finger will not prevent the individual from being granted access.
The biometric reader is comprised of the scanner which collects the fingerprint and converts it to a digital image, and the operating firmware/software referred to as the algorithm which determines which fingerprint characteristics are scanned, and also controls how the collected image is compared to the templates in the database.
How well the biometric system is working is measured in many different ways and is collectively referred to as performance metrics.
Down at the door, the system is judged by whether a person gets in or not, but of course there is a lot more involved, since sometimes someone not getting in is a good thing.
The basic performance metrics for biometric systems are:
False acceptance rate (FAR): the probability that the system incorrectly matches the input pattern to a non-matching template in the database.
False rejection rate (FRR): the probability that the system fails to detect a match between the input pattern and a matching template in the database.
There is extensive science associated with biometrics, which is readily available in the Locksmith Ledger archives and on the Internet.
One new biometrics entry is from Kaba Access and Data Systems Americas, a well-known company which offers comprehensive solutions for security at access points to buildings, containers, as well as for recording personal and enterprise data.
Kaba’s products utilize the latest technologies including remote access, biometrics, wireless, and GPS. Locksmith Ledger readers are probably already familiar with their other brands which include Kaba®, LA GARD, Simplex®, PowerPlex, and E-Plex®.
The AD102KIT Standalone Identity Access Management (I.AM) system features all the security benefits of biometric access control, but does not require a network or PC for programming or operation. The kit is comprised of an AD402 fingerprint key and a standalone controller which supports a single fingerprint reader but can control two separate entry points or devices.
The controller offers features consistent with other enterprise grade controllers, and programming protocol is similar to that of Kaba’s e-Plex line of door controllers. Programming is thru the AD402’s integral keypad.
Authenticated access or control is achieved in less than a second by placing an enrolled finger at the Fingerprint Key. As a backup to the fingerprint, or for visitors, keypad PIN access can be granted.
The Fingerprint Key is rated for indoor and outdoor use.
Similar to Kaba’s online networked systems, the applications are all embedded and require no software or servers.
Because of its competitive pricing and KABA quality engineering, security professions can feel confident deploying the AD102Kit for both residential and commercial applications including doors, gates, garages, warehouses, wine cellars, gun safes, jewelry cabinets, data rooms, remote sites and second properties.
Control of proprietary devices is also possible using the AD102KIT dry relay outputs. And it’s not just for offices or homes but also schools, restaurants, banks, retail and healthcare facilities.
The AD102KIT is designed to operate an external locking device or other equipment which requires a dry contact to control it. The controller comes with terminals required to achieve a fully operational single reader system. Although the system does not connect to a network, it is possible to remotely control the door, deactivate the system and monitor it for alarms and activity. No audit trail is possible unless the system is upgraded to a networked system (See coverage from the November 2013 Locksmith Ledger at www.locksmithledger/11191500.)
The basic elements to create a system are:
- AD102KIT Finger Lock and controller
- Power for the controller and reader
- Power for the electric locking device
- Door position sensor
- REX (Request to Exit device)
- Reset switch
- Locking device.
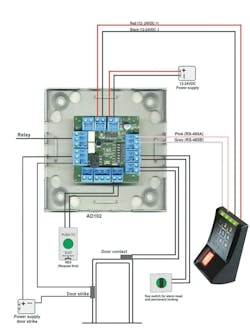
Typical connections and terminal assignments are shown on the accompanying wiring diagram.
The Standalone AD103KIT I.AM Kit supports one required Fingerprint Key (Kaba I.AM) reader through RS485 communication.
Reader Specifications:
Credentials: Fingerprint biometric, PIN
Templates: 50 user storage capacity
Search Modes: 1-to-many identification
Response/Reads: Enrollment <= 1 sec // Identification <= 1 sec
FAR & FRR: Adjustable
Fingerprint Sensor: Thin optical sensor, 500 dpi @ 8-bit per pixel, .55 x .87 in (14 x 22 mm) active area
Mechanical: IP65-listed, resin-sealed hard plastic enclosure, single-gang mount, metal mounting plate
Installation: Indoor/outdoor
Power Input: 12 to 24 VDC (24 VDC recommended) // Max.: 420 mA 12 VDC // Idle: 120 mA 12 VDC
Dimensions: 4.5 x 2.5 x 2 in (115 x 65 x 51 mm)
Operating Temperature: 14 to 122 °F (-10 to 50 °C); no direct sunlight
Relative Humidity: 0 to 95%, non-condensing
Controller Specifications:
Reader: Fingerprint Key (Kaba I.AM), 1 maximum
Access Points: 2 (via 1 supported Fingerprint Key)
Events: None (non-networked/offline module with embedded access software)
Mechanical: Metal mount plate with screw-on cover (standard). Rear, side cover access for cable connections. Mounts in standard third-party locking enclosures.
Installation: Environmentally controlled areas
PowerInput: 12 to 24 VDC (24 VDC recommended)
Load: 20 mA + current of connected reader 12 VDC
Dimensions: 4.7 x 4.7 x 1.5 in (120 x 120 x 40 mm) with enclosure
Packaged Weight: 1.59 lb (720 g):
Standalone Identity Access Management Kit (fingerprint key and controller) Specifications:
Operating Temperature: 32 to 122 °F (0 to 50 °C)
Relative Humidity: 0 to 85%, non-condensing
Interface: Readers: 1 x RS485 // 3 x input, 2 x output, 2 x relay // DC output (readers): 1 x 12-24 VDC
Controller Terminals:
- X1 DC-IN (12…24VDC) 2-pin
- X2 DC-OUT (Reader power) 2-pin
- X11 Reader RS-485 3-pin
- X8 OC-IN1 = Request to exit button 2-pin
- X9 OC-IN2 = Frame contact 2-pin
- X10 OC-IN3 = Alarm reset button 2-pin
- X4 Relay-2 = Alarm relay 3-pin
- X5 Relay-1 = Door strike relay 3-pin
Controller DIP Switch settings:
Various operating modes can be set with the DIP switch. To change the operating mode the device needs to be disconnected from power.
SW-1 Not in use; Must be set to OFF
SW-2 SW-7
ON OFF Operating mode "automatic pairing"
ON ON Operating mode "automatic pairing" and reset of administrator PIN to default "1234"
OFF OFF Door frame contact closed if door closed
OFF ON Door frame contact open if door closed
SW-3 Not in use
SW-4 Not in use. Must be set to OFF
SW-6 SW-5
OFF OFF Standard Mode
OFF ON Office / Party Mode
ON OFF Two Door Mode
ON ON Emergency Exit Mode
Status LEDs:
Two LEDs on the AD102 indicate:
LED V15 Indicates operating voltage
LED V2 Status LED
Flashing slowly (T = 1s): no connection to reader
Flashing rapidly (T = 0.5s): Connection to reader is established
For more information, contact your local locksmith distributor or Kaba, telephone 800-849-8324, Web Site www.kaba-adsamericas.com.
To read additional Locksmith Ledger articles on biometrics, visit http://tinyurl.com/biometrics214.