Customized Key Systems for Commercial Buildings and Applications
In today’s world of customization, generic solutions are no longer acceptable. That goes for everything from burgers to key systems. That’s why today’s buildings should adopt custom-designed key systems. This approach recognizes that only select doors require the highest measures of protection while others need a moderate level of access control.
Learn about the benefits of blending different grades of security cylinders within the same key system.
1. Protect High-Security Doors
Unlike consumer products at a retail store, commercial locksets with a “high security” label aren’t just a marketing ploy. This designation is verified through a third-party certification and adheres to UL 437 and ANSI/BHMA 156-3O. Manufacturers must demonstrate that products have been tested to withstand physical attacks such as picking and destructive tactics like drilling.
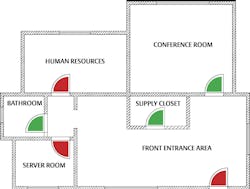
A high-security cylinder is ideal for doors that could be vulnerable to forced entry, such as:
- Perimeter doors, including main and side entrances
- A mechanical override for Electronic Access Control
- Exterior infrastructure, like fencing around generators
- Records storage
- IT rooms
- Pharmacies and storage for controlled substances
- Executive offices
- Hazardous waste storage
However, there are many interior doors where it doesn’t make sense to use a high-security cylinder, but maybe you would like to maintain one key convenience (aka unified key system). Think conference rooms, social areas like break rooms and kitchens, copier rooms, and private offices.
In many cases, you would have to maintain two key systems in order to support high-security doors and applications versus common areas. However, systems today allow you to blend high security and lower security (key control cylinders) all within the same unified key system, customizing the security level for each opening. It’s like buying a sports car when you really need a family vehicle – you don’t want to pay for heavy-duty performance where it’s not necessary.
2. Restrict Access on Medium-Security Doors
Certain doors should only be opened by approved users. These medium-security doors often include janitor and supply closets, roof access and maintenance areas. Even if it’s unlikely they’ll be exposed to a forceful attack, access control is still a priority.
These doors are also common for departments containing sensitive physical or electronic assets. This could be human resources, accounting, engineering and data science. Think about how many computers contain financial data, personnel records, or proprietary information. Many companies want to ensure intellectual property is under the proper lock and key.
If your facility has any number of medium-security doors, use a patented master key system. These patented keys can only be duplicated by authorized dealers or the manufacturer itself. Their complex designs and moving parts also deter copies being made from scans, photos, or 3D printing. The patent also extends to the door cylinder.
The best part about a patented key system is that it covers multiple levels of security cylinders within the same building. Patented keys can be used with doors regardless of the cylinder’s security grade. It means you can add medium-security locks to interior doors and still protect them with patented keys. It’s a budget-saving move that allows a facility to invest in high-security locksets only on entrances that truly need them.
3. Importance of Key Protection
Patents only last for 20 years. The patent applies to the key and its corresponding keyway, regardless if the cylinder is high or medium security. This safeguard means doors will be protected against illegal key duplication for the life of its patent.
Even with these mechanical and legal safeguards, best practices for key management are still critical. Regardless of the security level, a key system will inevitably degrade without proper policies in place. For example, if 10 of 100 keys have gone missing in a year, that means your system has a 10% vulnerability.
Start by creating a key control hierarchy to ensure users have the correct permissions and are issued the right key.
- Set procedures on how to assign and collect keys based on someone’s employment and authorization level.
- Document and enforce a key policy to prevent keys from being lost, stolen, or simply not returned upon staff turnover.
- Keep a complete inventory record, including a door audit, and update it regularly
Maintaining and auditing the key system and hardware greatly improves the long -term integrity of both and can be accomplished by using a key management tool like SimpleK. Without such a tool, the system will degrade at a rapid pace, maybe up to 20% per year, putting safety and security at needless risk and costing the facility more money in the long term.
Finally, review key permissions on an annual basis, regardless of whether someone was terminated or departed from the business. An existing keyholder’s authorization may need to be modified due to department reassignment, promotion, or other changes in job scope.
Security is only as good as the weakest link. Therefore, it’s important not to use easily-defeated locks to save on costs. Instead, build key systems with high- and medium-security locksets to secure buildings in a cost-effective manner.
4. Partner with a Local Security Professional
This article is intended to provide ideas on how to attain tightening up security at a reasonable budget, while maintaining the convenience of one patented key system. For further expertise and a unified solution, contact local security providers.
Certain manufacturers have a specialized customer base or a select group of customers that specialize in key systems and security applications. Do your research. Contact the manufacturer, find out who those local experts are, and make a connection. They can bring a lot of value to your next re-key or security project. These local resources can also guide you to a secure, fiscally friendly, protected system.
Dale L. Bowman, CML, CPP, PSP, PCI, LEED BD+C, is Medeco’s director of business development, OEM and international sales.
About the Author
Dale L. Bowman
Dale L. Bowman, CML, CPP, PSP, PCI, LEED BD+C, is Medeco’s director of business development, OEM and international sales.